windows
参考:https://mos86.com/40020.html
1、按下Windows键+R输入secpol.msc在运行对话框。单击确定打开安全策略管理单元。
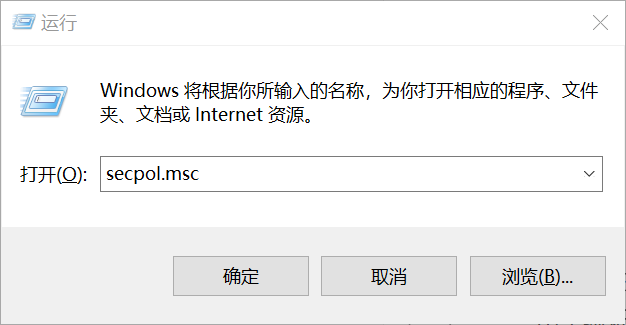
2.在本地安全策略管理单元中,单击公钥策略,找到证书路径验证设置
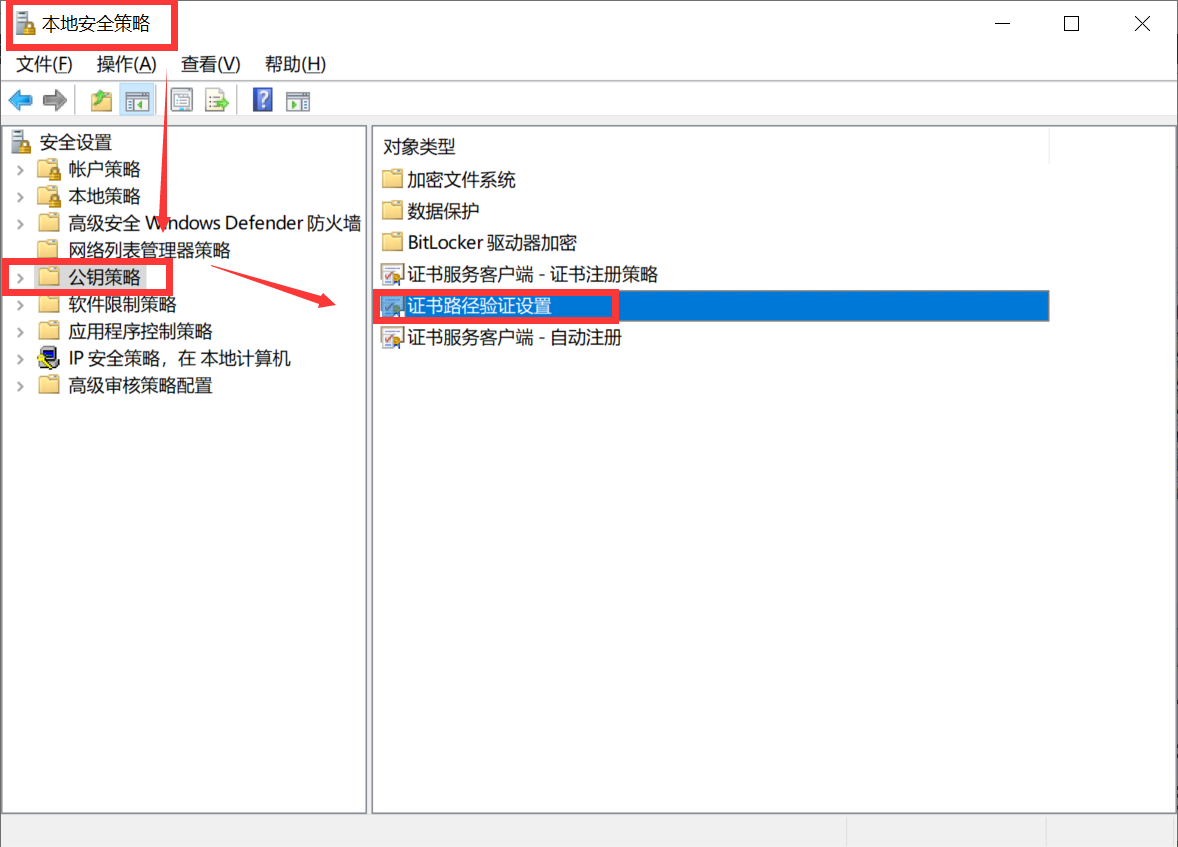
3.然后在证书路径验证设置属性中,选中定义这些策略设置。确保您选中允许用户受信任的根CA用于验证证书,并允许用户在此处信任对等信任证书选项。在根证书存储下,选择第三方根CA和企业根CA选项。单击应用,然后单击确定。
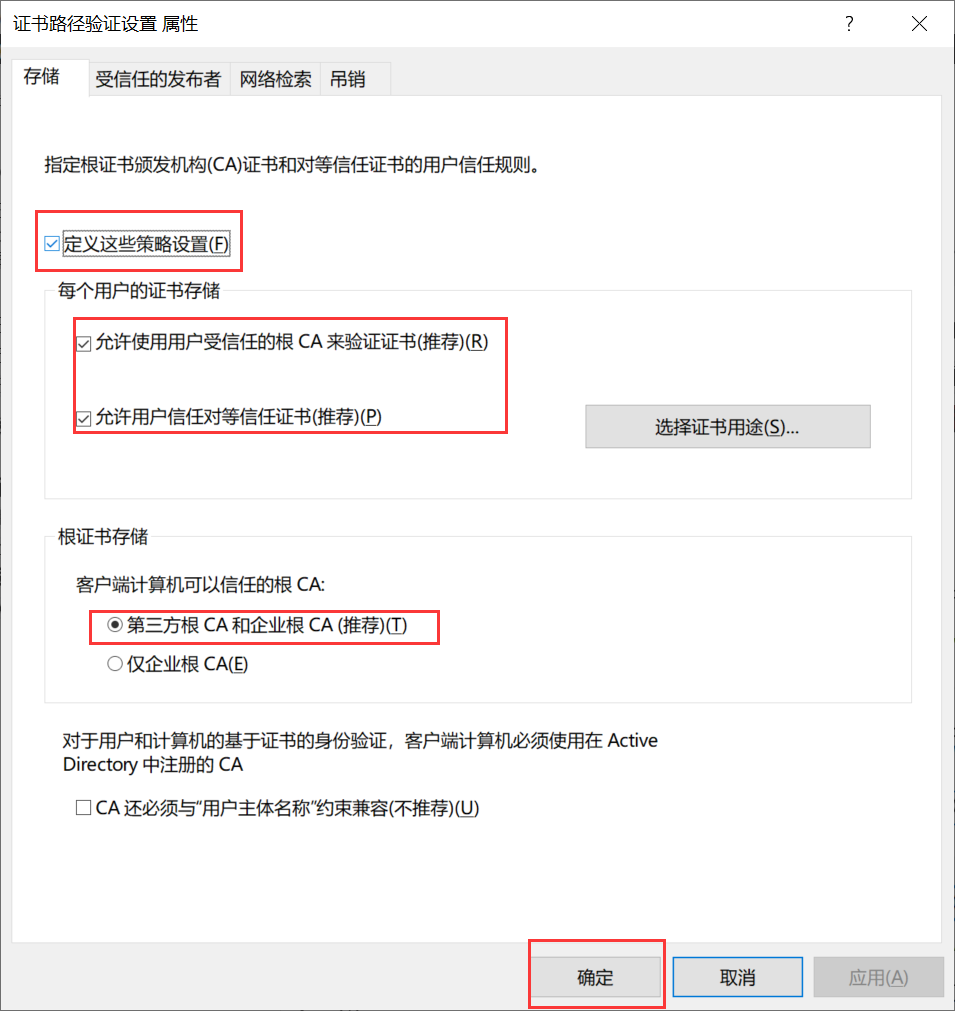
关闭本地安全策略管理单元。
4.按下Windows键+R输入certmgr.msc在运行对话框。
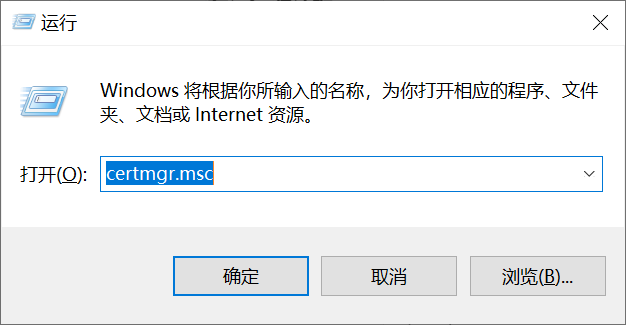
5.在证书管理器窗口中,单击受信任的根证书颁发机构右键单击证书并选择所有任务
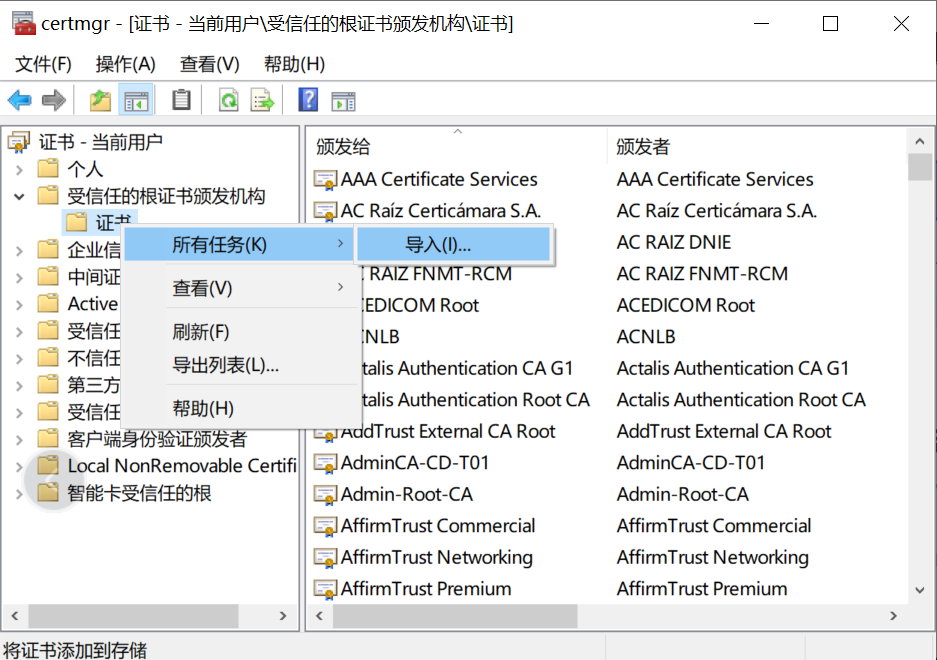
6.现在在证书导入向导中,单击下一步。
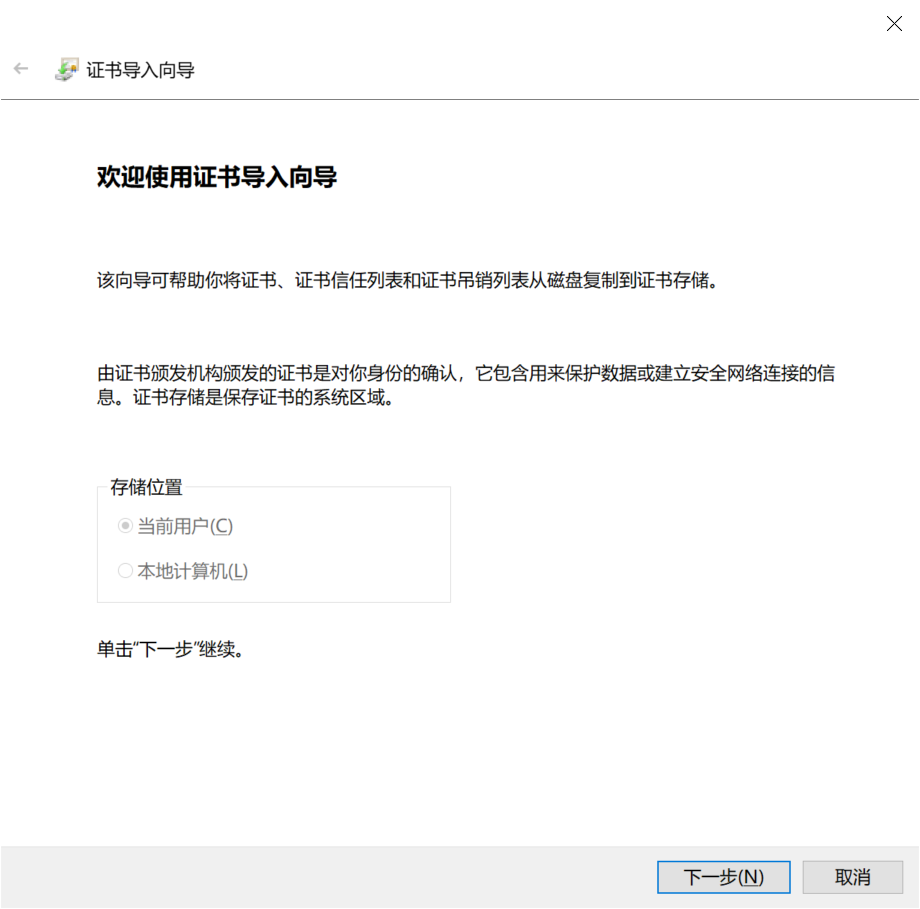
7.然后浏览证书根文件(请确保选择正确的文件格式.CRT )你从你的CA点击下一步。
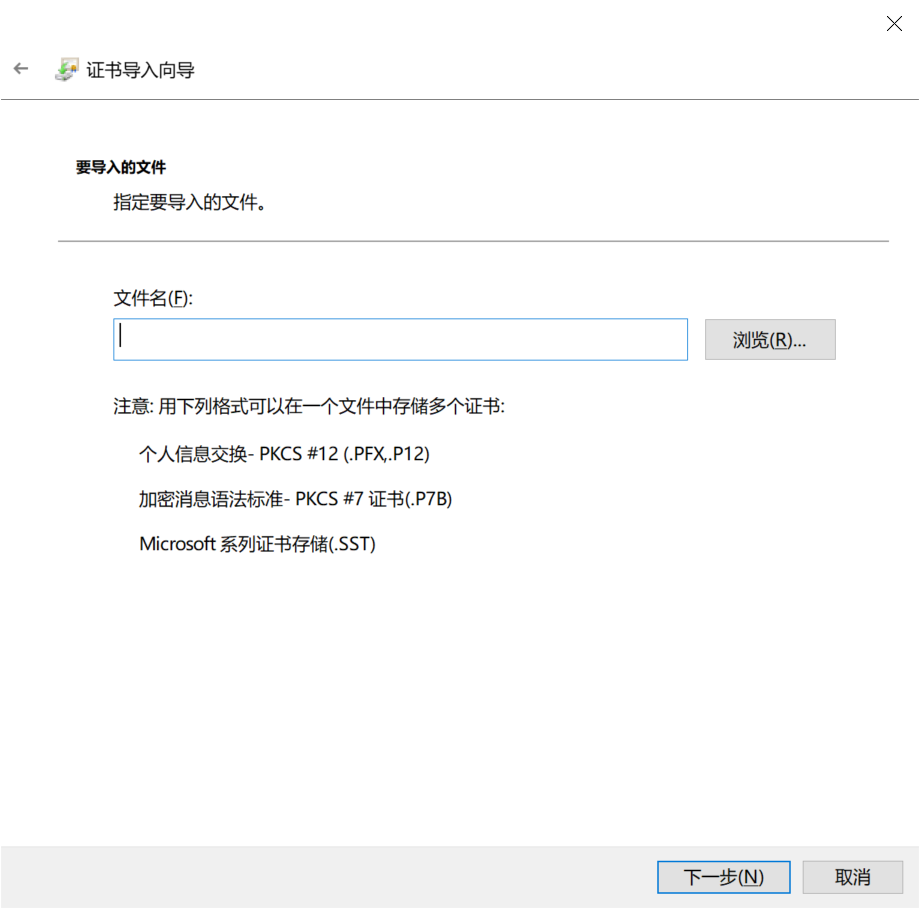
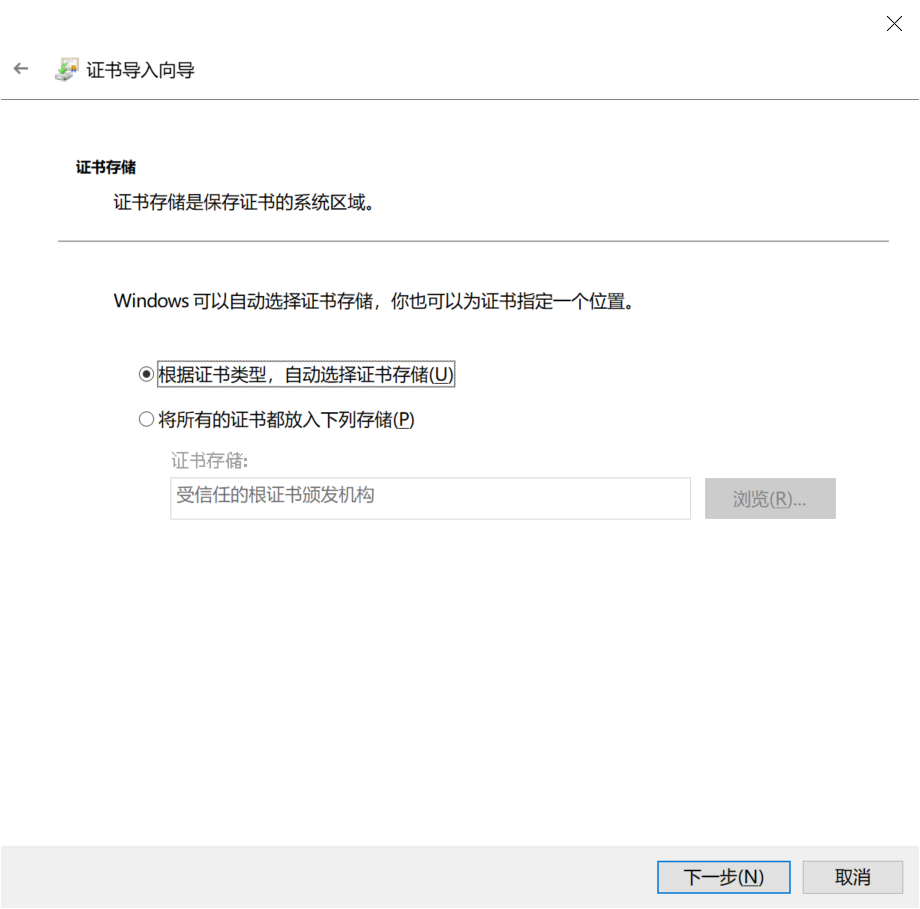
8.在下一个屏幕上,选择根据证书类型选项自动选择证书库。点击下一步。
9.单击完成以最终将证书导入到受信任的根证书颁发机构存储。
这样,您可以将新的受信任的根证书安装到Windows 10.
linux
以centos7为例:
把.crt格式的根CA证书放到下面这个目录里面就可以了
/etc/pki/ca-trust/source/anchors/
以ubuntu为例
1、将.crt格式的根CA证书放到/usr/local/share/ca-certificates下面
2、执行命令sudo update-ca-certificates
自签证书的脚本
脚本1
[root@xxx-01 certs-generator]# cat flush.sh gen.root.sh gen.cert.sh
#!/usr/bin/env bash
cd "$(dirname "${BASH_SOURCE[0]}")"
echo 'Removing dir out'
rm -rf out
echo 'Creating output structure'
mkdir out
cd out
mkdir newcerts
touch index.txt
echo "unique_subject = no" > index.txt.attr
echo 1000 > serial
echo 'Done'
#!/usr/bin/env bash
cd "$(dirname "${BASH_SOURCE[0]}")"
if [ -f "out/root.crt" ]; then
echo Root certificate already exists.
exit 1
fi
if [ ! -d "out" ]; then
bash flush.sh
fi
# Generate root cert along with root key
openssl req -config ca.cnf \
-newkey rsa:2048 -nodes -keyout out/root.key.pem \
-new -x509 -days 7300 -out out/root.crt \
-subj "/C=CN/ST=Shanghai/L=Pudong/O=IT/CN=service ROOT CA"
# Generate cert key
openssl genrsa -out "out/cert.key.pem" 2048
#!/usr/bin/env bash
if [ -z "$1" ]
then
echo
echo 'Issue a wildcard SSL certificate with Fishdrowned ROOT CA'
echo
echo 'Usage: ./gen.cert.sh <domain> [<domain2>] [<domain3>] [<domain4>] ...'
echo ' <domain> The domain name of your site, like "example.dev",'
echo ' you will get a certificate for *.example.dev'
echo ' Multiple domains are acceptable'
exit;
fi
SAN=""
for var in "$@"
do
SAN+="DNS:*.${var},DNS:${var},"
done
SAN=${SAN:0:${#SAN}-1}
# Move to root directory
cd "$(dirname "${BASH_SOURCE[0]}")"
# Generate root certificate if not exists
if [ ! -f "out/root.crt" ]; then
bash gen.root.sh
fi
# Create domain directory
BASE_DIR="out/$1"
TIME=`date +%Y%m%d-%H%M`
DIR="${BASE_DIR}/${TIME}"
mkdir -p ${DIR}
# Create CSR
openssl req -new -out "${DIR}/$1.csr.pem" \
-key out/cert.key.pem \
-reqexts SAN \
-config <(cat ca.cnf \
<(printf "[SAN]\nsubjectAltName=${SAN}")) \
-subj "/C=CN/ST=Shanghai/L=Pudong/O=IT/OU=$1/CN=*.$1"
# Issue certificate
# openssl ca -batch -config ./ca.cnf -notext -in "${DIR}/$1.csr.pem" -out "${DIR}/$1.cert.pem"
openssl ca -config ./ca.cnf -batch -notext \
-in "${DIR}/$1.csr.pem" \
-out "${DIR}/$1.crt" \
-cert ./out/root.crt \
-keyfile ./out/root.key.pem
# Chain certificate with CA
cat "${DIR}/$1.crt" ./out/root.crt > "${DIR}/$1.bundle.crt"
ln -snf "./${TIME}/$1.bundle.crt" "${BASE_DIR}/$1.bundle.crt"
ln -snf "./${TIME}/$1.crt" "${BASE_DIR}/$1.crt"
ln -snf "../cert.key.pem" "${BASE_DIR}/$1.key.pem"
ln -snf "../root.crt" "${BASE_DIR}/root.crt"
# Output certificates
echo
echo "Certificates are located in:"
LS=$([[ `ls --help | grep '\-\-color'` ]] && echo "ls --color" || echo "ls -G")
${LS} -la `pwd`/${BASE_DIR}/*.*
[root@xxx-01 certs-generator]# cat ca.cnf
[ ca ]
default_ca = Compass_ROOT_CA
[ Compass_ROOT_CA ]
new_certs_dir = ./out/newcerts
certificate = ./out/root.crt
database = ./out/index.txt
private_key = ./out/root.key.pem
serial = ./out/serial
unique_subject = no
default_days = 3650
default_md = sha256
policy = policy_loose
x509_extensions = ca_extensions
copy_extensions = copy
[ policy_loose ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ ca_extensions ]
basicConstraints = CA:false
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always
# subjectAltName = IP:127.0.0.1
keyUsage = digitalSignature,keyEncipherment
extendedKeyUsage = serverAuth
[ req ]
# Options for the `req` tool (`man req`).
default_bits = 2048
distinguished_name = req_distinguished_name
string_mask = utf8only
# SHA-1 is deprecated, so use SHA-2 instead.
default_md = sha256
# Extension to add when the -x509 option is used.
x509_extensions = v3_ca
[ req_distinguished_name ]
# See <https://en.wikipedia.org/wiki/Certificate_signing_request>.
countryName = Country Name (2 letter code)
stateOrProvinceName = State or Province Name
localityName = Locality Name
0.organizationName = Organization Name
organizationalUnitName = Organizational Unit Name
commonName = Common Name
emailAddress = Email Address
# Optionally, specify some defaults.
countryName_default = CN
stateOrProvinceName_default = Shanghai
localityName_default = IT
0.organizationName_default = Service
organizationalUnitName_default =
emailAddress_default =
[ v3_ca ]
# Extensions for a typical CA (`man x509v3_config`).
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ v3_intermediate_ca ]
# Extensions for a typical intermediate CA (`man x509v3_config`).
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always,issuer
basicConstraints = critical, CA:true, pathlen:0
keyUsage = critical, digitalSignature, cRLSign, keyCertSign
[ usr_cert ]
# Extensions for client certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = client, email
nsComment = "OpenSSL Generated Client Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
keyUsage = critical, nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = clientAuth, emailProtection
[ server_cert ]
# Extensions for server certificates (`man x509v3_config`).
basicConstraints = CA:FALSE
nsCertType = server
nsComment = "OpenSSL Generated Server Certificate"
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer:always
keyUsage = critical, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
[ ocsp ]
# Extension for OCSP signing certificates (`man ocsp`).
basicConstraints = CA:FALSE
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid,issuer
keyUsage = critical, digitalSignature
extendedKeyUsage = critical, OCSPSigning
或者去github找一些开源的脚本生成也可以,实在不行还可以用最传统的方法手动openssl生成证书
开源: https://github.com/llekn/openssl-ca
#简陋脚本
StandardOutput(){
echo -e "\033[1;32m$1\033[0m"
}
ErrorOutput(){
echo -e "\033[1;31m$1\033[0m"
}
read -e -p "请输入你的域名:" DOMAIN
mkdir ${DOMAIN} && cd ${DOMAIN}
(umask 077;openssl genrsa -out ca.key 2048)
openssl req -new -key ca.key -out ca.csr -subj "/C=CN/ST=Shanghai/L=Shanghai/O=Internet/OU=devops/CN=ca.${DOMAIN}"
openssl x509 -req -days 3650 -in ca.csr -signkey ca.key -out ca.crt
(umask 077;openssl genrsa -out ${DOMAIN}.key 2048)
openssl req -new -key ${DOMAIN}.key -out ${DOMAIN}.csr -subj "/C=CN/ST=Shanghai/L=Shanghai/O=Internet/OU=devops/CN=${DOMAIN}"
openssl x509 -req -days 3650 -in ${DOMAIN}.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out ${DOMAIN}.crt
StandardOutput "密钥文件路径: ${DOMAIN}/${DOMAIN}.key"
StandardOutput "证书文件路径: ${DOMAIN}/${DOMAIN}.crt"